
Dec 19, 2018
S/MIME: What is it, why should I care, and how does it relate to SparkPost?
S/MIME is a long-established method of sending encrypted, signed email, based on public Internet standards. We regularly come across requirements for S/MIME, particularly from regulated industries such as banking, health, and finance. S/MIME often is required when communicating between businesses and government agencies, for example.
Another secure mail standard, PGP (amusingly named as “Pretty Good Privacidad”), is used more for secure person-to-person communications. It’s less popular now because the consumer versions of popular web-based email clients such as Gmail and Outlook/Hotmail aren’t able to display encrypted mail. That’s one reason much person-to-person communication that requires privacy has moved to platforms such as WhatsApp (and many others) that offer native, end-to-end encryption.
Both PGP and S/MIME require a mail client that can use keys and certificates. Many desktop and mobile clients, including Correo de Apple, Microsoft Outlook, and Mozilla Thunderbird fit the bill, as do business versions of some web clients such as Microsoft Office 365. Setting up the keys takes work, but many organizations still consider it worthwhile, despite recent divulgación de vulnerabilidades requiring remedios to block loading of remote content.
S/MIME has been around since 1995 and gone through several revisions; the current version is covered by RFC 5751. It requires exchange of public keys, a non-trivial task that often requires the support of an IT team or similar resource. This is waquí commercial solutions from companies such as SparkPost partners Virtru and Echoworkx come in, making security easier for person-to-person business mailing (see our Cómo funciona SparkPost/Echoworkx for more information).
Dicho esto, profundicemos un poco más en el viejo S/MIME y veamos qué podemos hacer con él.
¿Por qué debería importarme?
La versión resumida:
La encriptación proporciona privacidad a los mensajes.
La firma proporciona autenticación (del remitente), no repudio del origen y comprobación de la integridad del mensaje.
S/MIME funciona de forma diferente a DKIM y DMARC y puede coexistir con ellos.
Privacidad
If your messages contain nothing personal, private, or legally important, then you probably won’t need to think about S/MIME. Modern email delivery systems such as SparkPost already use “TLS oportunista” to secure the message transport from sending server to recipient server.
En “opportunistic” part does mean however that if the sending server can’t negotiate a secure connection, we’ll send the mail in plain text. This isn’t suitable if you want to force the message to be secure all the way. You can take a peek at qué proveedores de buzones de correo declaran ser compatibles con TLS and which realmente lo hacen. Assuming the recipient’s server does support TLS, your message is secured así:

TLS asegura las conversaciones entre servidores de correo (por eso se llama Transport Layer Security). MIME (incluido S/MIME) se ocupa del contenido de los mensajes y su tratamiento, y puede considerarse parte de la "capa de presentación".
S/MIME secures the message content all the way (“end to end”) from the message origin a la recipient mail client, encapsulating the message body.
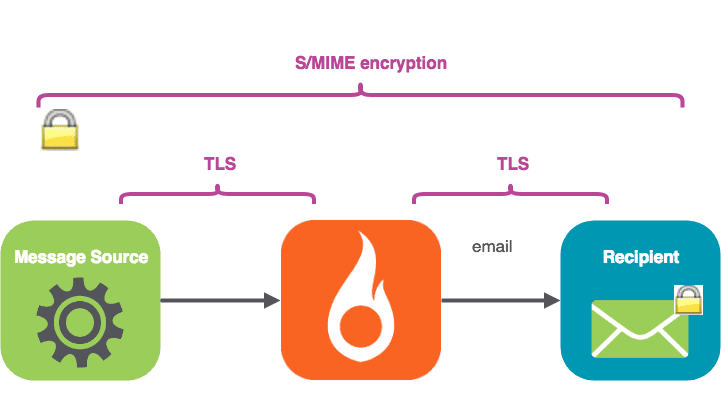
S/MIME cifra el cuerpo del mensaje con la clave pública del destinatario. El cuerpo del mensaje no puede descifrarse sin la clave privada del destinatario, ni por ninguna "persona en el medio", como su ISP, SparkPost o el servidor de correo del destinatario.
La clave privada nunca se revela; está en posesión exclusiva del destinatario. El mensaje cifrado viaja por Internet hasta el servidor de correo receptor. Cuando llega a la dirección inbox del destinatario, se desencripta (normalmente de forma automática) con su clave privada y pasa a ser legible.
Algunas trampas de S/MIME a tener en cuenta:
El cifrado S/MIME tiene el efecto secundario de impedir el escaneado de mensajes entrantes basado en servidor en busca de malware, ya que la carga útil del mensaje está cifrada y, por tanto, no es identificable.
Note that the message cabeceras (From:, To:, Subject: etc) are not encrypted, so the subject-line content needs to be created with that in mind.
Firma - autenticación
S/MIME also provides the recipient the ability to check that the identity of the message sender es quien dice ser.
En sender’s email has a certificate attached, which, rather like the certificate on a secure website, can be traced back to an issuing authority. Taquí’s a full description of the signing process aquí.
Primero firmaremos el correo y luego lo cifraremos, así que el proceso será el siguiente.
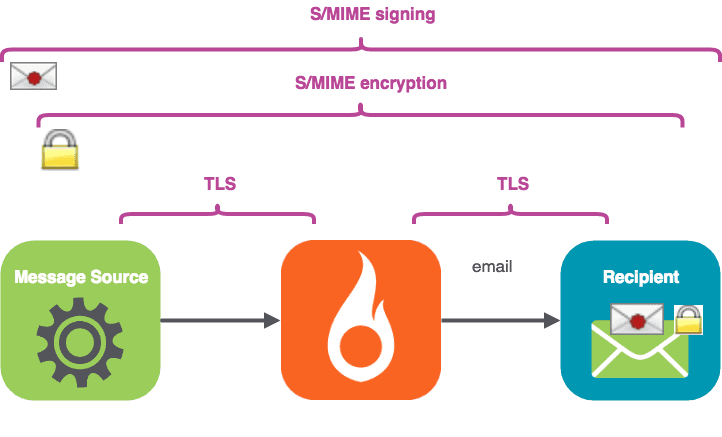
No repudio
Another useful benefit of signing a la recipient is non-repudiation of origin. Consider a situation waquí an email message is used to approve a contract. The recipient gets the contract in a message from the sender. If the sender later tries to say, “Nope, I never sent that message to you”, then the received message shows that the sender’s certificate was in fact used.
Integridad de los mensajes
The signing process creates a fingerprint of the plain source message (known as a message digest), encrypts the digest using the sender’s private key, and includes it in the delivered message. The recipient’s mail client can tell if the message body is tampered with.
Perhaps you might say, “I thought DKIM gives me message integrity checks!” Well yes, DKIM provides message body and message header integrity checks – anti-tampering guarantees. However, DKIM failure (or absence) will not usually cause the incoming message to be marked as completely invalid, …unless a DMARC policy of `p=reject` is in play (more on DMARC here). DKIM is one factor of many used by the ISP for reliable assignment of reputation to a domain and is, of course, an essential part of your messaging stack.
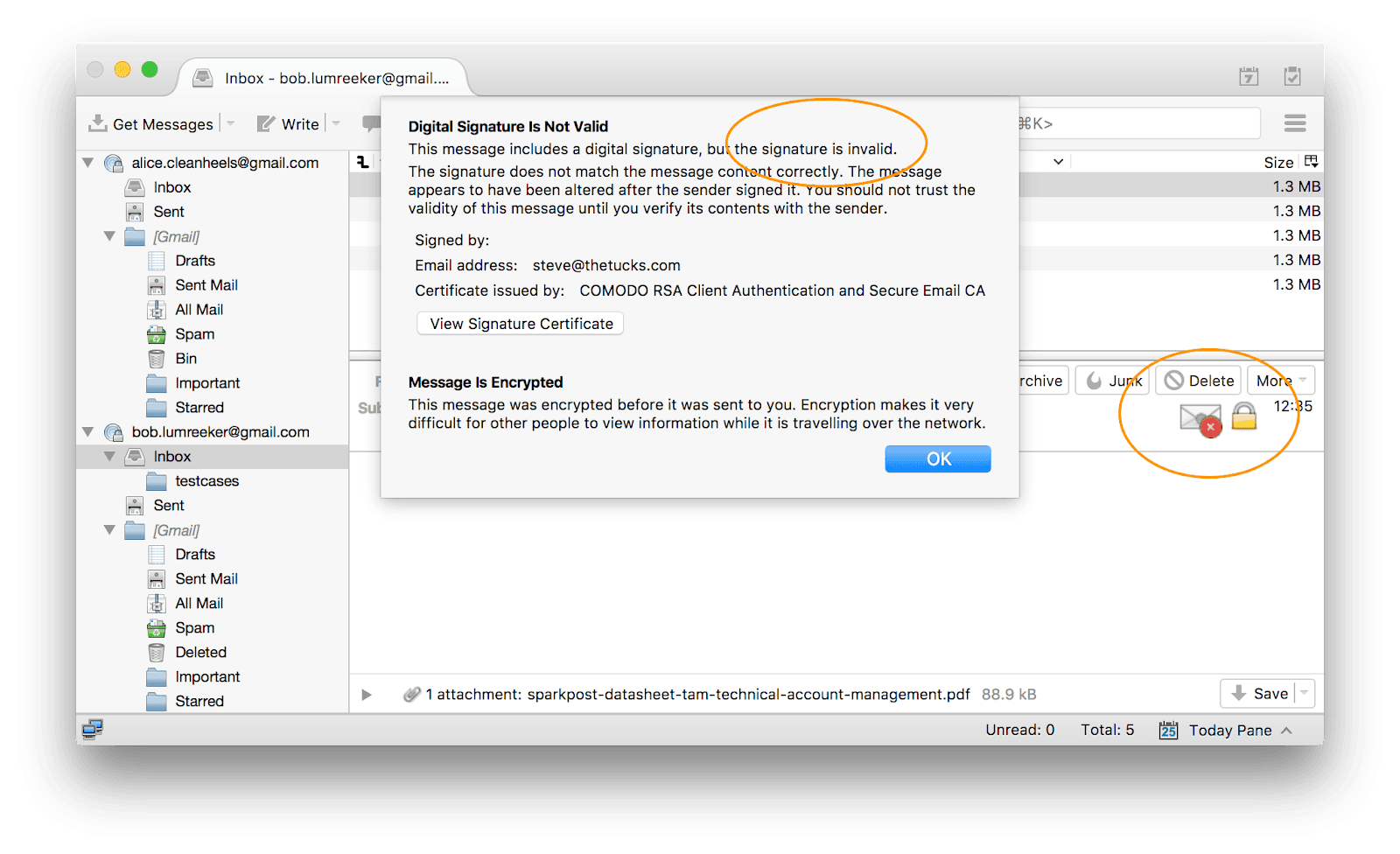
Su cliente de correo le mostrará de forma destacada si un mensaje S/MIME falla la comprobación de firma:
Resumen: extremo a extremo (S/MIME) frente a servidor a servidor (DKIM, DMARC, TLS)
S/MIME is a presentation-layer capability that can work between two email end-users (with valid certificates/keys) without any action by the email admin. S/MIME provides encryption and signing and is personal to each user.
S/MIME is tied to the full sending address (local part and domain part), so, for example, alice@bigcorp.com and bob@bigcorp.com would need to have different certificates. In contrast, DKIM validates the email is coming from the signing domain. DKIM is a whole subject in itself; este artículo is a good place to start.
La configuración de DKIM y DMARC la realiza su administrador de correo electrónico (trabajando en el servidor de correo y los registros DNS). Una vez configurados, están activos para dominios, no para usuarios individuales.
¿Qué relación tiene esto con SparkPost?
Mail systems for person-to-person messaging, such as Microsoft Exchange Server, have S/MIME compatible desde hace tiempo.
Si está utilizando SparkPost para enviar a destinatarios específicos con clientes de correo que puedan leer S/MIME, entonces podría tener sentido firmar sus mensajes con S/MIME. La firma S/MIME añade una garantía adicional de que el mensaje procede realmente de ti (o de tu sistema) y no ha sido manipulado, lo que puede ser valioso en algunos casos de uso. Todo lo que necesitas para ello es tu propia clave y algo de software libre que demostraremos en la parte 2 de este artículo.
Utilizar el cifrado S/MIME es otra opción. Necesitarás la clave pública de cada uno de tus destinatarios. Obtenerla puede ser tan fácil como pedirles que te envíen (a ti o a tu aplicación) un correo electrónico firmado. Exploraremos una herramienta práctica para enviar correo firmado y encriptado S/MIME a través de SparkPost en un post posterior.
¿Qué clientes admiten S/MIME?
Consumidores Gmail
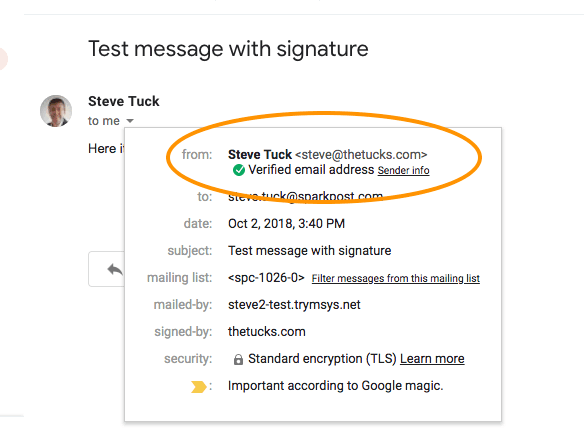
The ordinary Gmail web client displays incoming mail signatures (see below), but it’s not set up to hold your private key to read encrypted messages. Even if that were possible via third-party plugins, uploading your private key is not a great idea from a security standpoint.
No he conseguido que Yahoo Mail descodifique las firmas de los mensajes.
La versión para consumidores de las cuentas de Microsoft Outlook/Hotmail le avisan de la presencia de una firma S/MIME, pero no le dan acceso completo para ver o comprobar el certificado.
Correo profesional alojado
For organizations with hosted mail, Microsoft Office 365 and G Suite Enterprise have S/MIME support.
Clientes de correo Outlook
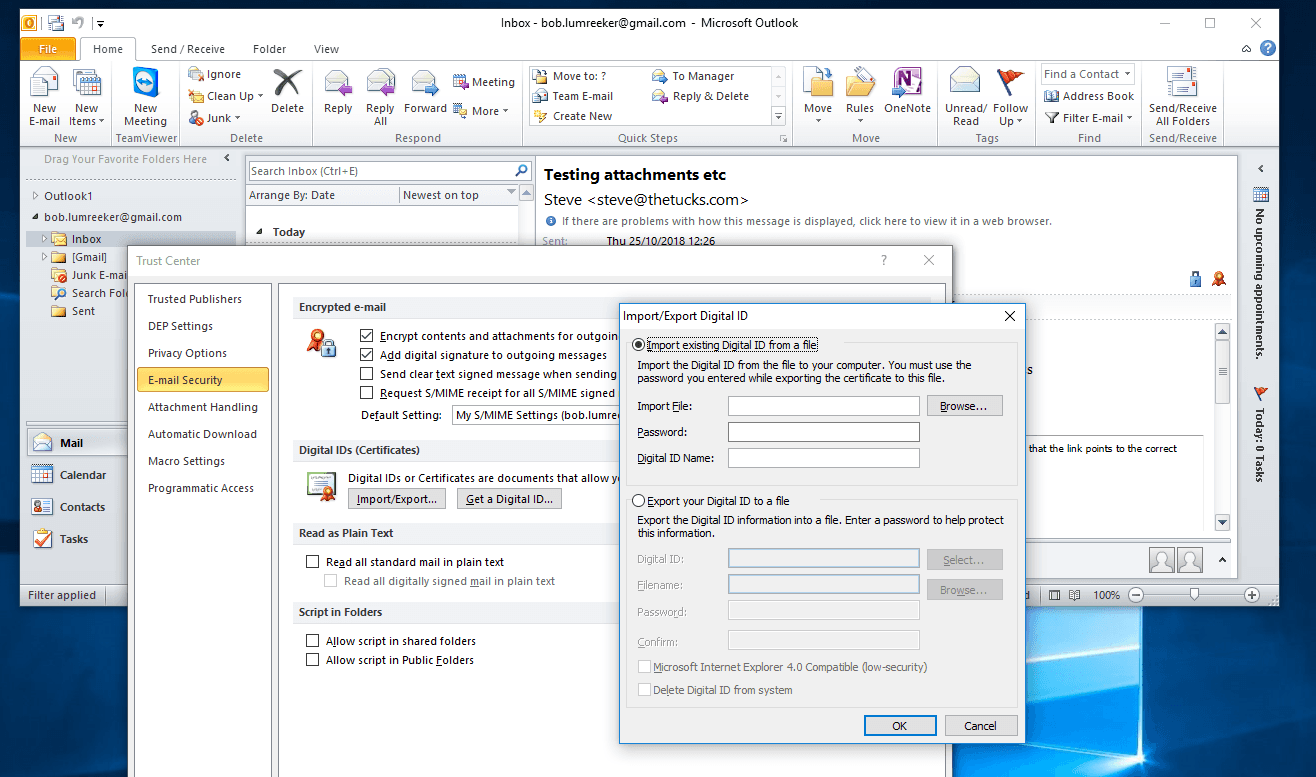
Client-based Microsoft Outlook (e.g. 2010 for Windows) works:
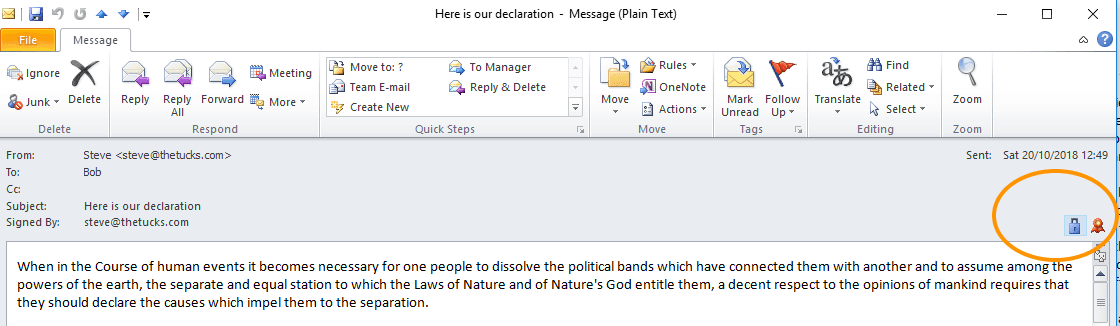
Si hace clic en los iconos, obtendrá más información:
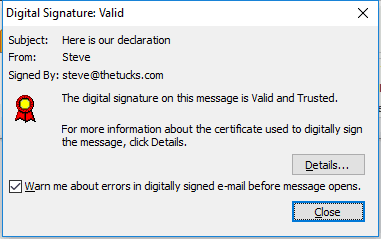
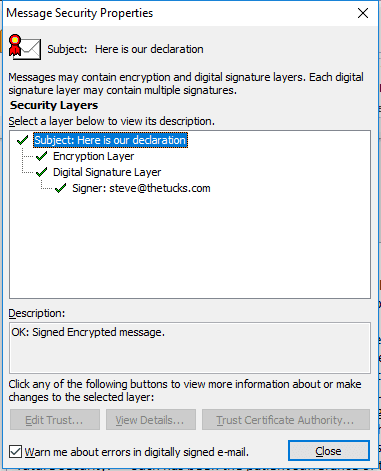
En Outlook 2010 / Windows, se accede al almacén de certificados a través de Archivo / Opciones / Centro de confianza / Configuración del Centro de confianza / Seguridad del correo electrónico / Importar / Exportar.
Thunderbird - multiplataforma y gratuito
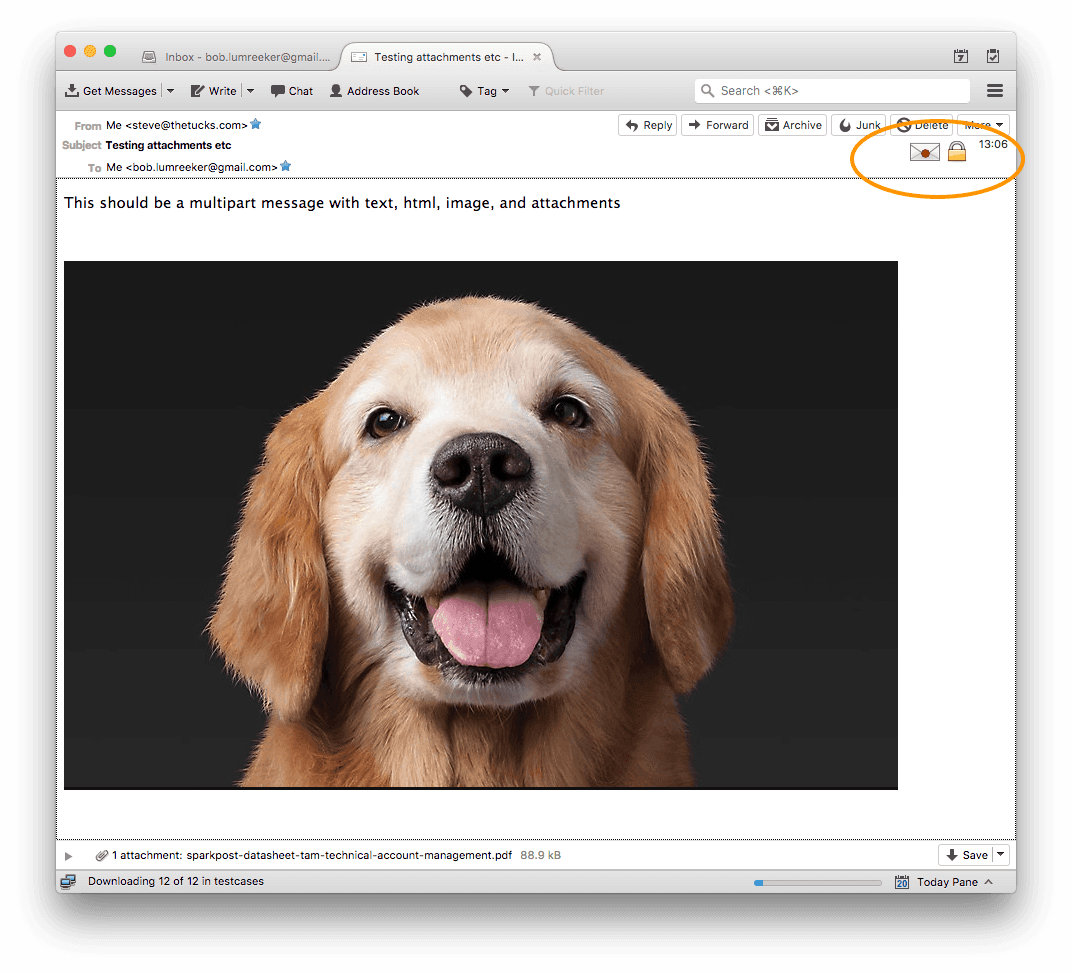
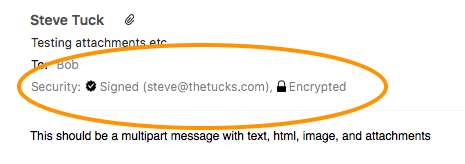
If you’re looking for a free client, Mozilla Thunderbird fits the bill. It’s available on PC, Mac, and Linux, and supports S/MIME across all of these. Here’s how a message looks on Mac. The “sealed envelope” icon indicates the message is signed, and the padlock indicates it was encrypted.
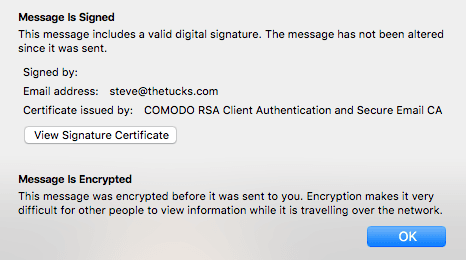
Al hacer clic en el sobre/bloqueo se muestra información sobre el mensaje:
Thunderbird has its own key store, accessed in similar ways on each platform:
Mac via Preferences / Advanced / Certificates / Manage Certificates
PC: menu (“hamburger” top right), Advanced / Certificates / Manage Certificates
Linux: menu (“hamburger” top right), Preferences / Advanced / Manage Certificates
Correo Mac
Mac Mail also supports S/MIME. It relies on your Mac keychain to hold your keys.
Correo iOS
Firstly, import your email account’s certificate like this, then you can view S/MIME signed and encrypted emails. They don’t really look any different on the viewing screen.


Android
Algunos devices and apps support S/MIME; there’s a lot of variety out there. Samsung has a guide.
Finalmente...
That’s our quick overview of the practical uses of S/MIME. If you want to get your own mail certificates, there’s a list of providers here. I found Comodo works well (free for non-commercial use – open this in Firefox, not Chrome).
En la parte 2, exploraremos cómo aplicar la firma y el cifrado S/MIME a los mensajes que envíe a través de SparkPost.
Para saber más
Microsoft has a good introductory article on S/MIME here.
For more info on the EFAIL vulnerability and how it’s been addressed, this is the definitive site. Other easy-to-follow explanations are here and here.